General information on NTP
Before we continue with NTP Daemon linux setup few words on Network Time Protocol (NTP). It is a networking protocol for clock synchronization between computer systems over packet-switched, variable-latency data networks. In operation since before 1985, NTP is one of the oldest Internet protocols in current use. Network Time Protocol is syncing all participating computers to within a few milliseconds of specified timezone (system clock with a trusted external source) and is critical for many services out there: Distributed systems, Loggers, LoadBalancers, etc. For more details on the protocol, you can also check RFC 5905 NTPv4 Specification (IETF).
NTPd is always actively adjusting the time. A sudden change in time can be problematic for many services/daemons, so NTPd is speeding up the length of a second or slowing it down to bring the time into sync gradually (recommended way of correcting it). Ntpd checks with its configured time servers on a regular basis, usually between 64 and 1024 seconds (by default) depending on the stability of the local and remote clock.
For good list of sources you can use for sync, check NTP Pool Project.
NTP provides a time service using UDP port 123.
Configuration file: /etc/ntp.conf
NTP Daemon Linux Setup
First of all, install NTP.
CentOS:
yum install ntp ntpdata
Ubuntu:
sudo apt-get install ntp
Add servers to /etc/ntp.conf
# Use public servers from the pool.ntp.org project. # Please consider joining the pool (http://www.pool.ntp.org/join.html). server 0.centos.pool.ntp.org iburst server 1.centos.pool.ntp.org iburst server 2.centos.pool.ntp.org iburst server 3.centos.pool.ntp.org iburst
Feel free to replace servers with the ones you select. The iburst option (recommendation by NTP Pool) will send a burst of eight packets instead of the usual one packet, in case server is unreachable. The burst option can be abusive (sending 8 packets every pool interval), so try to avoid it.
NTP Vulnerability
The monlist feature in ntp_request.c in ntpd in NTP before 4.2.7p26 allows remote attackers to cause a denial of service (traffic amplification). Test it:
ntpdc -n -c monlist localhost
If you see something like:
ntpdc: read: Connection refused
You’re ok, but If you see a list of server addresses:
remote address port local address count m ver rstr avgint lstint =============================================================================== ...
your server is responding to the MONLIST attack. To prevent this, add following lines to /etc/ntp.conf
# By default, exchange time with everybody, but don't allow configuration. restrict -4 default kod notrap nomodify nopeer noquery limited restrict -6 default kod notrap nomodify nopeer noquery limited disable monitor
As always, keep your security above everything else and keep an eye on NTP vulnerabilities.
ntpd uses the restrict command to control access. The restrict command sets the access to “all”, then applies each of the listed restrictions. So, by default everyone will get an unrestricted access. Therefore, if you don’t need your NTP server to respond on public IP, add:
restrict 127.0.0.1 restrict ::1
Note: ntpd supports IPv6. Commands containing IPv4 addresses are optionally marked with “-4” (cmds with IPv6 addresses => “-6”). If you are running IPv6 and you don’t know it, then there is a chance no access restriction is applied there. In the most recent ntpd releases the syntax has been unified and address type detection occurs automatically. In any case, it’s worth mentioning this, for general awareness.
NTP Configuration file flags/parameters
kod limited
The kod option means a “Kiss-o’-death” packet is to be sent to reduce unwanted queries. If you only set kod, nothing will happen (ignored). There is no rate limiting. If you only set limited, rate limiting will be enabled (excessive queries will be dropped, but KoD replies will not be sent). If you set both kod and limited (sometimes excessive queries will be silently dropped, sometimes KoD replies will be sent). Use discard cmd to tune rate managemnt and mru maxmem cmd to control amount of memory algorithm uses.
nomodify– forbids any changes to the configuration.notrap– prevents ntpdc control message protocol traps (The trap service is a subsystem of the ntpdq control message protocol which is intended for use by remote event logging programs).nopeer– doesn’t allow forming of a peer association .noquery– prevents answers for ntpq and ntpdc queries, but not for time queries
In this NTP Daemon Linux Setup guide we’re not going into much details, we’re just covering some basic segments. There are more than enough flags to play around for a while, but we’re skipping them for now.
Finish
Finally, turn on the service:
chkconfig ntpd on
In regard to OS/environment, start NTP (restart if already running):
/etc/init.d/ntpd restart
sudo systemctl restart ntp.service
Use default client to list peers:
ntpq -p
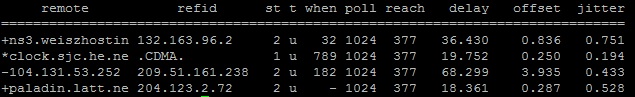
Column details
remote– remote server you wish to synchronize your clock withrefid– upstream stratum to the remote server. For stratum 1 servers, this will be the stratum 0 source.st– stratum level, 0 through 16.t– connection type. Can be “u” for unicast or manycast, “b” for broadcast or multicast, “l” for local reference clock, “s” for symmetric peer, “A” for a manycast server, “B” for a broadcast server, or “M” for a multicast serverwhen– last time when the server was queried for the time.- Default: seconds
- “m” for minutes
- “h” for hours
- “d” for days.
poll– How often the server is queried for the time, with a minimum of 16 seconds to a maximum of 36 hours, also can be displayed as a value from a power of two. Typically, it’s between 64 seconds and 1024 seconds.reach– 8-bit left shift octal value that shows the success and failure rate of communicating with the remote server (On Success – bit is set, On Failure – bit is not set. 377 is the highest value)delay– showing the round trip time (RTT) of your computer communicating with the remote server (in ms).offset– using root mean squares, and shows how far off your clock is from the reported time the server gave you. It can be positive or negative (also in ms).jitter– showing the root mean squared deviation of your offsets (also in ms, but an absolute value).
Row details
- ” ” Discarded as not valid. Could be that you cannot communicate with the remote machine (it’s not online), this time source is a “.LOCL.” refid time source, it’s a high stratum server, or the remote server is using this computer as an NTP server.
- “
x” Dismissed by the intersection algorithm. - “
.” Discarded by table overflow (not used). - “
-” Dismissed by the cluster algorithm. - “
+” Included in the combine algorithm (a good candidate if the current server we are synchronizing with is discarded for any reason). - “
#” Good remote server to be used as an alternative backup. Only shown if you have more than 10 remote servers. - “
*” The current system peer. This is marking a remote server as a time source to syncrhonize system clock. - “
o” Pulse per second (PPS) peer (Codes “o” and “*” will not be displayed simultaneously)
Column/Row details acquired on pthree.org.
NTP Daemon Linux Setup, over and out..
Things to work on:
- Check timezone adjustment.



