Termshark: Terminal UI for TShark
Introduction
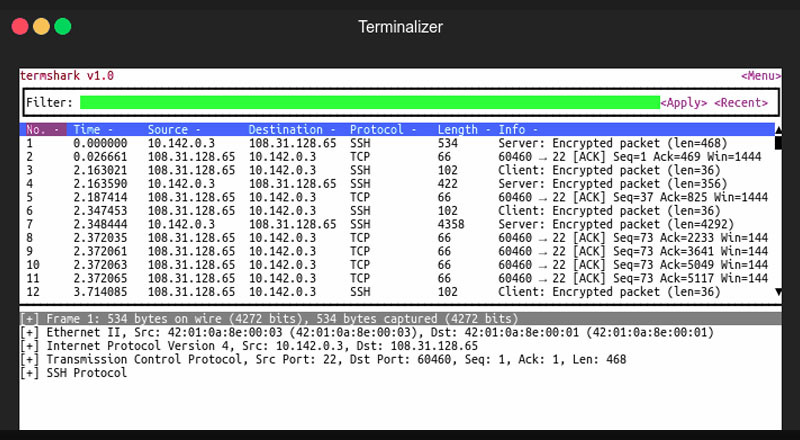
Termshark is the latest terminal user-interface tor Tshark, a network protocol analyzer that ranks among the best of its kind. It was developed as an inspiration from Wireshark which is a free cross-platform and open source network protocol analyzer. Termshark is basically the futuristic terminal version of Wireshark.
Qt (graphical user interface library), a very popular Promiscuous Capture Library (libpcap), a packet capture and filtering library.Check out WireShark: The World’s Foremost Network Protocol Analyzer for details and installation instructions.
Termshark: Simple Terminal UI for Tshark
As a terminal user interface, Termshark can come in handy when carrying out debugging operations on a remote machine that has a fairly large pcap (Packet Capture). If you do not intend to copy all the converted signals onto your desktop Termshark can effectively assist you.
Termshark is written in Go, this gives it its lightweight and effective feature which enables it to perfectly integrate with Tshark forming a synchronized interactive unit. In simple terms, Termshark acts as the interactive terminal interface which Tshark lacks. When combined the duo form one single interactive terminal-based software that can assist you carry out network protocol analysis at a microscopic level.
With this new interface, data packets in the network traffic can be critically analyzed, and because it is written with one of the simplest programming languages, Termshark is very easy to use. Since its release, users have reported having a good experience while using this terminal interface.
This is probably due to the amazing keyboard shortcuts that the developers included in its build, for example: you can easily switch in between panes by using TAB, and if you want to display filters – use /, etc.
Features:
- Read
pcapfiles or sniff live interfaces (where tshark is permitted). - Inspect each packet using familiar Wireshark-inspired views
- Filter
pcapsor live captures using Wireshark’s display filters - Copy ranges of packets to the clipboard from the terminal
- Written in
Go, compiles to a single executable on each platform – downloads available for Linux (+termux), OS X, FreeBSD, and Windows
Supported Platforms:
- Linux (Arch Linux, Ubuntu, Debian, LinuxMint, etc. ), OS X, Windows
Termshark Dependencies:
tshark,tcell,gowid
Install
Linux
Before installing Termshark you must ensure that your machine has Tshark installed. To download Tshark run:
$ sudo apt install tshark
Clone the Termshark repo from the GitHub:
$ git clone https://github.com/gcla/termshark.git
Then extract the files to /usr/local/bin and complete the installation by running the following command:
$ sudo install termshark /usr/local/bin/
OS X
To install TSark on OS X, use brew:
$ brew install wireshark
Usage
To list all available options, use -h:
$ termshark -h
termshark v1.0.0
A wireshark-inspired terminal user interface for tshark. Analyze network traffic interactively from your terminal.
See https://github.com/gcla/termshark for more information.
Usage:
termshark [FilterOrFile]
Application Options:
-i=<interface> Interface to read.
-r=<file> Pcap file to read.
-d=<layer type>==<selector>,<decode-as protocol> Specify dissection of layer type.
-Y=<displaY filter> Apply display filter.
-f=<capture filter> Apply capture filter.
--pass-thru=[yes|no|auto|true|false] Run tshark instead (auto => if stdout is not a tty). (default: auto)
--log-tty=[yes|no|true|false] Log to the terminal.. (default: false)
-h, --help Show this help message.
-v, --version Show version information.
Arguments:
FilterOrFile: Filter (capture for iface, display for pcap), or pcap file to read.
If --pass-thru is true (or auto, and stdout is not a tty), tshark will be
executed with the supplied command- line flags. You can provide
tshark-specific flags and they will be passed through to tshark (-n, -d, -T,
etc). For example:
$ termshark -r file.pcap -T psml -n | less
Examples:
Inspecting a local pcap:
$ termshark -r test.pcap
To capture ping packages on interface eth0:
$ termshark -i eth0 icmp
Reading from an interface and applying tcp:
$ termshark -i enp4s0 tcp




