Zydra: Password Recovery | Linux Shadow File Cracker

Introduction
Zydra is a tool that has the ability to perform password recovery operations and can also cracker user passwords which are available in the Linux shadow file. The tool is written in python and is capable of deploying both brute force and dictionary search in cracking user passwords.
Zydra: File Password Recovery Tool and Linux Shadow File Cracker
With its multiprocessing feature zydra makes use of all the available core processors, this helps in speeding up the rate at which passwords are cracked. Zydra supports different file formats and this makes it even more useful when it comes to decrypting passwords. It supports:
- legacy zip files, RAR files, PDF files and Linux shadow files.
Its ability to support the Linux shadow files gives it an added advantage in cracking user passwords in shadow format.
In deploying brute force on a user password zydra will randomly generate all the potential keys that it can use to access the password information of the user. The keys are generated at high speeds due to the availability of multiprocessing feature when used on a user account the password of the victim will be easily accessed in no time.
All attack processes can be viewed from the progress bar so you can know how much time is remaining for zydra to crack the intended password. This feature can come in handy when cracking passwords under limited time frames. It can help you know whether you should abort the procedure or continue with the attack.
Features
- Supports brute force attack and dictionary search
- Can run on multiple processors
- Allows specification of characters (in brute force attack)
- Error handling
- Allows specification of password length (in brute force attack)
Supported Platforms
- Linux
Prerequisites
Python 3.3+qpdfandunrarpackages- Debian-based distro (recommended Kali Linux)
- Python modules:
py-term,zipfile,pyfiglet,rarfile,cryp, etc. (usepip3to install)
Install Zydra
Clone it from the GitHub:
$ git clone https://github.com/hamedA2/Zydra.git
Usage
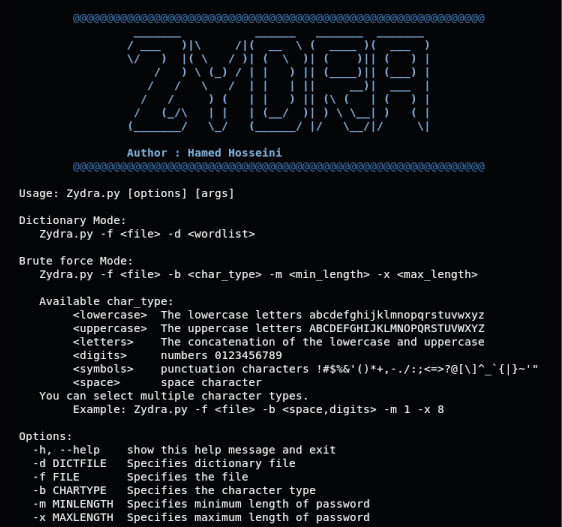
To list all available options, use -h:
$ python3 Zydra.py -h
Examples
Performing a dictionary search for a zip file password:
$ python3 Zydra.py –f file.zip –d example.txt
Accessing user password using brute force on a shadow file:
$ python3 Zydra.py –f shadow –b digits,symbols –m 4 –x 4



![Cyber Jacking [Attack Types] Cyber Jacking [Attack Types]](https://cdn.cyberpunk.rs/wp-content/uploads/2019/06/cyberjacking_bg-500x275.jpg)